- Open portal.azure.com -> Click “Azure Active Directory”.
- In the Monitoring section, click “Sign-ins”.
- Click Download -> CSV.
- Import the resulting file into Microsoft Excel:
- In Excel, click File -> Open –> Choose the file you just downloaded.
- In the Text Import Wizard, choose Data Type = “Delimited” and tick the “My data has headers” box -> Click Next.
- In the Delimiters section, tick “Comma” -> Click Next.
- Scroll through the fields preview and choose “Do not import column (skip)”, leaving only following columns: Date (UTC), User, Username, IP address, Location, Status. (For more logon details, you can also leave the “Application”, “Resource”, “Authentication requirement”, “Browser”, “Operating System” fields checked.) -> Click “Finish”.
- Filter by trusted locations (or IP addresses) using the “Location” (or “IP address”) column.
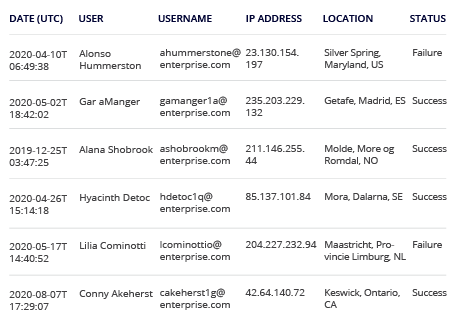
- Review the results:
1. Run Netwrix Auditor → Navigate to "Search" → Specify the following criteria:
- Filter – "Data source"
Operator – "Equals"
Value – "Azure AD" - Filter – "Object type"
Operator – "Equals"
Value – "Logon" - Filter – "Workstation"
Operator – "Does not contain"
Value – An IP address or location to be excluded
You can exclude several IP addresses or locations by adding additional “Workstation” filters.
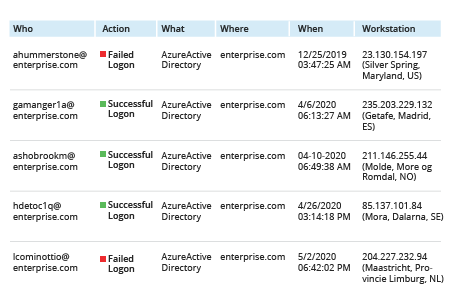
2. Click “Search”:
To save this report for future use, click “Tools” -> Click “Save as report” -> Specify a name for your report ‑> Click “Save”.
