- From the Azure portal menu, select Monitoring, or search for and select Monitoring from any page.
- Select Audit Logs.
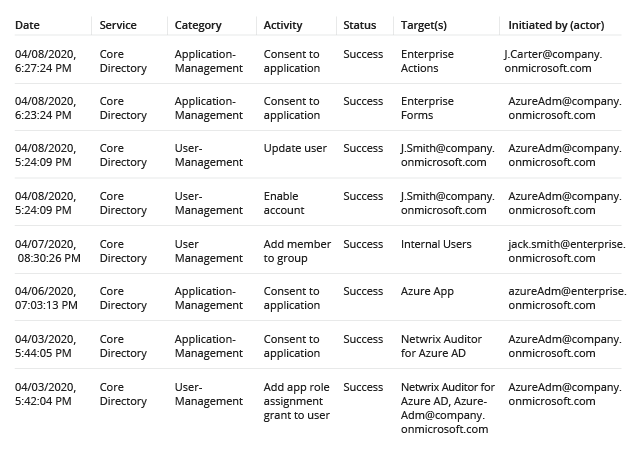
- Filter the report to show only application-related events by picking "Application Management" in the Category column’s search section. The Target(s) column shows the application name.
- Review the event details in the Details tab at the bottom of the page.
Note: If you want to filter out whitelisted applications, you will have to pull the log data into a CSV file and analyze it manually, since the native event log filters don’t have an exclude function.
- Run Netwrix Auditor → Navigate to “Search” → Click “Advanced mode” if it is not automatically selected → Set up the following filter: “Data source” "Equal" “Azure AD”.
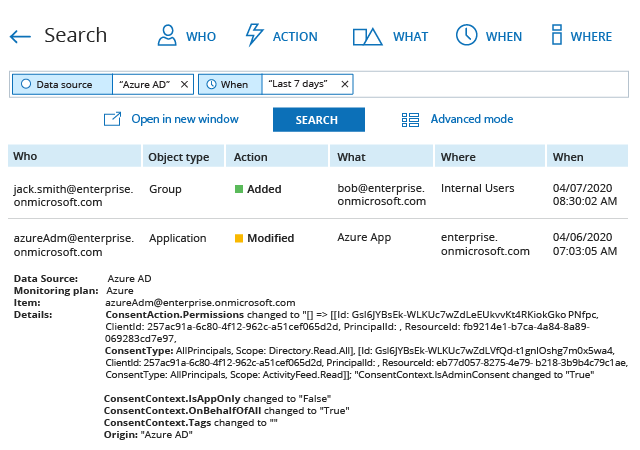
- Refine your search results to applications only by adding the filter “Object Type” = “Application”, and exclude any whitelisted application by adding the following filter:
Filter = “What”
Operator = “ Not Equal”
Value = “App Name”
